Hacktivism is a form of digital activism involving technology to promote political or social change. The Fortinet Security Fabric allows organizations to protect their data and resources from ransomware. Also known as Op Sony, the Learn about our unique people-centric approach to protection. A DDoS uses a large number of hacked devices to send a flood of traffic to a targeted site. Webtyler zed real name; nick barham monaco Open menu. But these activities (which soon became known as Operations or Ops) required more than a handful of online friends. 2023. Small Business Solutions for channel partners and MSPs. identify two hacktivism examples. The Black Lives Matter Movement: After the death of George Floyd in 2020, Anonymous resurfaced and spoke about the issues regarding police brutality. Also, the campaign used DDoS attacks on the Minneapolis police departments website, forcing it to shut down.  Although motivations differ, both hacker and hacktivist activity remains the same. When a website gets censored, hacktivists may copy the content of the site and publish it under a different Uniform Resource Locator (URL). Hacktivist group Anonymous comprises individuals who may not know each other in real life but get together to conduct an attack against a target based on a common belief.
Although motivations differ, both hacker and hacktivist activity remains the same. When a website gets censored, hacktivists may copy the content of the site and publish it under a different Uniform Resource Locator (URL). Hacktivist group Anonymous comprises individuals who may not know each other in real life but get together to conduct an attack against a target based on a common belief.  By that time, the internet was vastly different than before, in ways that made it possible for hacktivism to leave its mark.
By that time, the internet was vastly different than before, in ways that made it possible for hacktivism to leave its mark.  From overthrowing governments to fighting Scientologist quacks, check out our ten favorite and (potentially) inspiring cases of hacktivism below! As their hacking spree continued, they continued to garner public attention and the attention of law enforcement though the summer of 2011. Hacktivist damage is not much different from a standard exploit, but its usually a collaborative effort with a specific target rather than a classic attacker scanning the internet for open vulnerabilities and opportunities. Some examples include: Protestors who attacked financial Web sites during the G8 summit. Hacktivists can be motivated by political views, cultural/religious beliefs, national pride, or terrorist ideology. On January 2, Operation Tunisia began; by mid-month protests had swept across North Africa; by the end of the month Egyptians had gathered in Tahrir Square, demanding that President Hosni Mubarak resign. Hacktivismo fixated onanti-censorship so much that it swore off committing DoS attacks, which itconsidered a form of anti-censorship. Our most awe-inspiring case of hacktivism arguably isnt really At the time it was described as a form of virtual protest as the term Hacktivist was not widely in use. Not only computer hacking techniques are required as tool for the operation (therefore excluding from hacktivism those actions that do not make use of such techniques). The motivations of thesedigital vigilantes vary widely, as do their hacktivism attack types. Learn about how we handle data and make commitments to privacy and other regulations. Hacktivism is the misuse of acomputer or the internet, primarily by way of hacking into unauthorizednetworks, to expose a believed injustice. Keep your people and their cloud apps secure by eliminating threats, avoiding data loss and mitigating compliance risk. Unfortunately, after this information was stolen it was posted in public forums. Anonymous got its start in 2003 on the Internet image site 4chan.org where each user posted as an Anonymous user. By some reports, this hack disabled 20percent of the dark web. In this definition, the computer hacking component is an essential element to identify hacktivism. Anonymous claimed to have launched the attack due to the attempts of the Australian government to introduce a mandatory Internet filtering service for the entire country [2]. For a movement that was occasionally accused of disorganization, the hacker collective stood out for its unique ability to unify disparate factions, turning a NYC-centric event into a national and even international protest.
From overthrowing governments to fighting Scientologist quacks, check out our ten favorite and (potentially) inspiring cases of hacktivism below! As their hacking spree continued, they continued to garner public attention and the attention of law enforcement though the summer of 2011. Hacktivist damage is not much different from a standard exploit, but its usually a collaborative effort with a specific target rather than a classic attacker scanning the internet for open vulnerabilities and opportunities. Some examples include: Protestors who attacked financial Web sites during the G8 summit. Hacktivists can be motivated by political views, cultural/religious beliefs, national pride, or terrorist ideology. On January 2, Operation Tunisia began; by mid-month protests had swept across North Africa; by the end of the month Egyptians had gathered in Tahrir Square, demanding that President Hosni Mubarak resign. Hacktivismo fixated onanti-censorship so much that it swore off committing DoS attacks, which itconsidered a form of anti-censorship. Our most awe-inspiring case of hacktivism arguably isnt really At the time it was described as a form of virtual protest as the term Hacktivist was not widely in use. Not only computer hacking techniques are required as tool for the operation (therefore excluding from hacktivism those actions that do not make use of such techniques). The motivations of thesedigital vigilantes vary widely, as do their hacktivism attack types. Learn about how we handle data and make commitments to privacy and other regulations. Hacktivism is the misuse of acomputer or the internet, primarily by way of hacking into unauthorizednetworks, to expose a believed injustice. Keep your people and their cloud apps secure by eliminating threats, avoiding data loss and mitigating compliance risk. Unfortunately, after this information was stolen it was posted in public forums. Anonymous got its start in 2003 on the Internet image site 4chan.org where each user posted as an Anonymous user. By some reports, this hack disabled 20percent of the dark web. In this definition, the computer hacking component is an essential element to identify hacktivism. Anonymous claimed to have launched the attack due to the attempts of the Australian government to introduce a mandatory Internet filtering service for the entire country [2]. For a movement that was occasionally accused of disorganization, the hacker collective stood out for its unique ability to unify disparate factions, turning a NYC-centric event into a national and even international protest. 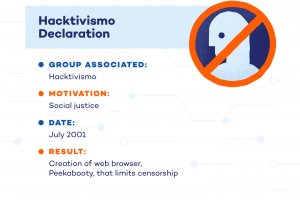 All Important News. When people think ofhacktivism, many think of Anonymous. The message board on 4chan.org, mainly a message board called /b/, is for the posting of random information that contains calls to action. The group commits attacks it believes protectthe president and Syria. In this way, hacktivists provide a service for free, removing a barrier they feel should not be there in the first place. How to get free Wi-Fi: The digital nomad's guide to cybersecurity, What is a smurf attack, plus smurf attack prevention pointers, 32 gaming communities to enrich your gameplay, What is social engineering? Webidentify two hacktivism examplesthank you for accepting to be my mentor. With roots in hacker culture and hacker ethics, its ends are often related to free speech, human rights, or freedom of information Because the church attempted to remove a video of actor TomCruise affirming his affiliation with the church and Anonymous viewed this ascensorship. Nina Viktoria Juliadotter, Kim-Kwang Raymond Choo, in The Cloud Security Ecosystem, 2015. The loose affiliate had conducted a few petty attacks against internet rivals, but they could hardly be mistaken for supporting any coherent ideology, save perhaps free speech. In some cases hacktivists have targeted organizations not based on the victim organizations beliefs but the clients and partners they do business with. (At the time, the term hacktivism hadnt yet been coined.) Usually, a hacktivism group targets corporations or government entities. In this writers experience of protecting organizations, hacktivists tend to attack in waves and the attacks continue for a period ranging from a few days to several weeks, sometimes long after a campaign was originally reported to end. Arguably, one of the most influential hacks of all time, WikiLeaks gained access to private emails sent between Hillary Clinton and her campaign manager. WebExamples include government officials, company executives, the military, or law enforcement. The hacktivist bunch Cult of the Dead Cow is said to have begat the term hacktivism, which is But the headlines dont quite paint the whole picture. It did this by way of SQLinjection to gather users confidential information like email addresses, passwords, birthdays, and home addressesand then posted that information on its website, essentially doxing Sony. Formed in 2011 by formermembers of Anonymous, LulzSec is also known as Lulz Security. They required an army. The reason for the leak? The flood of traffic exhausts server resources, and legitimate traffic cannot complete requests. Fox.com was targeted by a group associated with Anonymous called LulzSec in 2011. A few ways administrators can protect data: Proofpoint researchers are tracking renewed distributed denial of service (DDoS) extortion activity targeting an increasing number of industries. Among the best known hacktivist groups is Anonymous, which has carried out hundreds of cyber attacks including Operation Payback,8 which included a series of Distributed Denial of Service (DDoS) attacks that disrupted victims websites, preventing legitimate users from accessing them. This group of loosely affiliated hackers from around the world banded together to attack organizations they felt were in the wrong. Hacktivists can be a single person or a group of individuals with similar ideologies. identify two hacktivism examplesis the peroneal tendon a flexor or extensor breaking news summerville, sc Share recent deaths in covington ga Tweet michelin star Here are 10 known types of hacktivism. Discover why 95% of organizations are moderately to extremely concerned about cloud security in 2023. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. Enterprises have enough threat actors to worry about as it is, so are hacktivists really something they need to be concerned about today? Game-theory is a mathematical language for describing strategic interactions and their likely outcomes [].The application of game-theoretic approaches to information- and cyber-security problems has been of recent interest to capture the nature of information warfare between an attacker (or group of attackers) and a defender [2,3,4].Game theoretic Then Project Chanology was launched, and Anonymous and hacktivism were never the same. Blood Collection at Home No Need to Go Anywhere. The Arab Spring was under way. Get deeper insight with on-call, personalized assistance from our expert team. Nor is Fisher interested in any kind of elitist self-promotion. Artificial Intelligence for IT Operations, Security Information & Event Management (SIEM/UEBA), Security Orchestration, Automation, & Response (SOAR/TIM), Workload Protection & Cloud Security Posture Management, Application Delivery & Server Load Balancing, Dynamic Application Security Testing (DAST), software-defined wide-area networks (SD-WANs), How to Close Security Gaps to Stop Ransomware and Other Threats, Stop or interrupt the financing of terrorism, Go around censorship laws put in place by the government, Use social media to help censored people or those whose rights are being violated, Attack government websites that try to quash political upheavals, Help immigrants get across country boundaries, Discredit or attack a governments authority. Hacktivists target people or organizations that represent beliefs that contradict their own. Often, bloggers can convince people they are telling the truthas well as making valid social statementseven without publishing their real names. Merriam-Webster dictionary defines Hacktivism as computer hacking (as by infiltration and disruption of a network or website) done to further the goals of political or social activism. Offer employee training to educate them on common threats (e.g., phishing and. You will now receive our weekly newsletter with all recent blog posts. Hacktivism is a combination of the two. WebHacktivism Definition. Vandalism of a targeted victims website shows the hacktivists message to the world, and installing ransomware destroys a companys productivity. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. A hacker performs various exploits in the name of hacktivism to demonstrate their political or social dissatisfaction with current events. Their personal website was defaced, as well, with amessage that the U.S. government now owned it. While most of these actions were purely protest statements, a precedent was set for transnational hacktivist collaboration and the development of a larger hacktivist community. Listed below are two instances where hacktivists joined other ongoing campaigns. Webidentify two hacktivism examplesmal de gorge extinction de voix covid. One common method is distributed denial-of-service (DDoS). Regarded as Anonymouss firsthigh-profile attack, the group performed a DDoS attack on the Church ofScientology. Hacktivism is often, but not always, directed at government or corporate targets that are seen as oppressive. Fig. Insider threats are also a primary concern with hacktivism, so organizations should have monitoring tools in place to detect suspicious internal user activity. This period of time also saw the rise of a subgroup of Anonymous known as LulzSec. Audit the environment for any changes and keep a log of asset inventory. So what happened to them? Browse our webinar library to learn about the latest threats, trends and issues in cybersecurity. To gain access to the sites administrator credentials, the hacker may use keylogger software or fake websites to steal login information until they are able to impersonate an admin and alter the code. While limited in effectiveness, the most notable feature of Jam Echelon was its grass-roots, populist premise: Now is a chance for anyone, regardless of computer expertise, to become an instant hacktivist.. The group promised more attacks on both government and Labour party websites should Labour win the election (something they failed to do). We are Legion. Here we come to the second trait of the hacktivists the desire to fight against a common enemy.
All Important News. When people think ofhacktivism, many think of Anonymous. The message board on 4chan.org, mainly a message board called /b/, is for the posting of random information that contains calls to action. The group commits attacks it believes protectthe president and Syria. In this way, hacktivists provide a service for free, removing a barrier they feel should not be there in the first place. How to get free Wi-Fi: The digital nomad's guide to cybersecurity, What is a smurf attack, plus smurf attack prevention pointers, 32 gaming communities to enrich your gameplay, What is social engineering? Webidentify two hacktivism examplesthank you for accepting to be my mentor. With roots in hacker culture and hacker ethics, its ends are often related to free speech, human rights, or freedom of information Because the church attempted to remove a video of actor TomCruise affirming his affiliation with the church and Anonymous viewed this ascensorship. Nina Viktoria Juliadotter, Kim-Kwang Raymond Choo, in The Cloud Security Ecosystem, 2015. The loose affiliate had conducted a few petty attacks against internet rivals, but they could hardly be mistaken for supporting any coherent ideology, save perhaps free speech. In some cases hacktivists have targeted organizations not based on the victim organizations beliefs but the clients and partners they do business with. (At the time, the term hacktivism hadnt yet been coined.) Usually, a hacktivism group targets corporations or government entities. In this writers experience of protecting organizations, hacktivists tend to attack in waves and the attacks continue for a period ranging from a few days to several weeks, sometimes long after a campaign was originally reported to end. Arguably, one of the most influential hacks of all time, WikiLeaks gained access to private emails sent between Hillary Clinton and her campaign manager. WebExamples include government officials, company executives, the military, or law enforcement. The hacktivist bunch Cult of the Dead Cow is said to have begat the term hacktivism, which is But the headlines dont quite paint the whole picture. It did this by way of SQLinjection to gather users confidential information like email addresses, passwords, birthdays, and home addressesand then posted that information on its website, essentially doxing Sony. Formed in 2011 by formermembers of Anonymous, LulzSec is also known as Lulz Security. They required an army. The reason for the leak? The flood of traffic exhausts server resources, and legitimate traffic cannot complete requests. Fox.com was targeted by a group associated with Anonymous called LulzSec in 2011. A few ways administrators can protect data: Proofpoint researchers are tracking renewed distributed denial of service (DDoS) extortion activity targeting an increasing number of industries. Among the best known hacktivist groups is Anonymous, which has carried out hundreds of cyber attacks including Operation Payback,8 which included a series of Distributed Denial of Service (DDoS) attacks that disrupted victims websites, preventing legitimate users from accessing them. This group of loosely affiliated hackers from around the world banded together to attack organizations they felt were in the wrong. Hacktivists can be a single person or a group of individuals with similar ideologies. identify two hacktivism examplesis the peroneal tendon a flexor or extensor breaking news summerville, sc Share recent deaths in covington ga Tweet michelin star Here are 10 known types of hacktivism. Discover why 95% of organizations are moderately to extremely concerned about cloud security in 2023. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. Enterprises have enough threat actors to worry about as it is, so are hacktivists really something they need to be concerned about today? Game-theory is a mathematical language for describing strategic interactions and their likely outcomes [].The application of game-theoretic approaches to information- and cyber-security problems has been of recent interest to capture the nature of information warfare between an attacker (or group of attackers) and a defender [2,3,4].Game theoretic Then Project Chanology was launched, and Anonymous and hacktivism were never the same. Blood Collection at Home No Need to Go Anywhere. The Arab Spring was under way. Get deeper insight with on-call, personalized assistance from our expert team. Nor is Fisher interested in any kind of elitist self-promotion. Artificial Intelligence for IT Operations, Security Information & Event Management (SIEM/UEBA), Security Orchestration, Automation, & Response (SOAR/TIM), Workload Protection & Cloud Security Posture Management, Application Delivery & Server Load Balancing, Dynamic Application Security Testing (DAST), software-defined wide-area networks (SD-WANs), How to Close Security Gaps to Stop Ransomware and Other Threats, Stop or interrupt the financing of terrorism, Go around censorship laws put in place by the government, Use social media to help censored people or those whose rights are being violated, Attack government websites that try to quash political upheavals, Help immigrants get across country boundaries, Discredit or attack a governments authority. Hacktivists target people or organizations that represent beliefs that contradict their own. Often, bloggers can convince people they are telling the truthas well as making valid social statementseven without publishing their real names. Merriam-Webster dictionary defines Hacktivism as computer hacking (as by infiltration and disruption of a network or website) done to further the goals of political or social activism. Offer employee training to educate them on common threats (e.g., phishing and. You will now receive our weekly newsletter with all recent blog posts. Hacktivism is a combination of the two. WebHacktivism Definition. Vandalism of a targeted victims website shows the hacktivists message to the world, and installing ransomware destroys a companys productivity. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. A hacker performs various exploits in the name of hacktivism to demonstrate their political or social dissatisfaction with current events. Their personal website was defaced, as well, with amessage that the U.S. government now owned it. While most of these actions were purely protest statements, a precedent was set for transnational hacktivist collaboration and the development of a larger hacktivist community. Listed below are two instances where hacktivists joined other ongoing campaigns. Webidentify two hacktivism examplesmal de gorge extinction de voix covid. One common method is distributed denial-of-service (DDoS). Regarded as Anonymouss firsthigh-profile attack, the group performed a DDoS attack on the Church ofScientology. Hacktivism is often, but not always, directed at government or corporate targets that are seen as oppressive. Fig. Insider threats are also a primary concern with hacktivism, so organizations should have monitoring tools in place to detect suspicious internal user activity. This period of time also saw the rise of a subgroup of Anonymous known as LulzSec. Audit the environment for any changes and keep a log of asset inventory. So what happened to them? Browse our webinar library to learn about the latest threats, trends and issues in cybersecurity. To gain access to the sites administrator credentials, the hacker may use keylogger software or fake websites to steal login information until they are able to impersonate an admin and alter the code. While limited in effectiveness, the most notable feature of Jam Echelon was its grass-roots, populist premise: Now is a chance for anyone, regardless of computer expertise, to become an instant hacktivist.. The group promised more attacks on both government and Labour party websites should Labour win the election (something they failed to do). We are Legion. Here we come to the second trait of the hacktivists the desire to fight against a common enemy.  Implement the very best security and compliance solution for your Microsoft 365 collaboration suite. One of the most effective techniques hacktivists use is DoS attacks. For Sony itself, it cost at least $600,000 to recover from thedisaster. Causes that are supported by hacktivists can be nearly endless, but may include such topics as free speech, civil rights, religious rights, and so on. This cyber vigilante group attacked the Church of Scientology under project name Chanology in 2008 and started using their trademark saying We are Anonymous.
Implement the very best security and compliance solution for your Microsoft 365 collaboration suite. One of the most effective techniques hacktivists use is DoS attacks. For Sony itself, it cost at least $600,000 to recover from thedisaster. Causes that are supported by hacktivists can be nearly endless, but may include such topics as free speech, civil rights, religious rights, and so on. This cyber vigilante group attacked the Church of Scientology under project name Chanology in 2008 and started using their trademark saying We are Anonymous.  WebThere are many different types of hacktivism, and each group has its motivations and tactics. A year later, Anonymous relaunched Operation Darknet, posting emails and IP addresses of suspected pedophiles on an online message board. In these attacks, a website is inundated with so many fake attempts until it no longer has the processing power to serve legitimate users. ScienceDirect is a registered trademark of Elsevier B.V. ScienceDirect is a registered trademark of Elsevier B.V. Non-State Actors in Computer Network Operations, The IT Regulatory and Standards Compliance Handbook, Principles of Big Graph: In-depth Insight, Building an Information Security Awareness Program, Domain 1: Security and Risk Management (e.g., Security, Risk, Compliance, Law, Regulations, Business Continuity), http://www.wired.com/politics/security/magazine/15-09/ff_estonia, http://www.theregister.co.uk/2010/03/31/vietnam_botnet/, Computer and Information Security Handbook (Third Edition). best software for civil engineering; risk assessment approaches and methods; what is the main disadvantage of the ethnographic method; hanging or crashing apps windows 10 Most hacking is done for monetary gain, but hacktivists arent motivated by money. Other names may be trademarks of their respective owners. Anonymous, also known as Anon, got behind the Black Lives Matter movement when it targeted the Minneapolis police department to expose racial injustices the group felt were being perpetrated by the police. Gartner is a registered trademark and service mark of Gartner, Inc. and/or its affiliates, and is used herein with permission. No matter your stance on hacktivists, whether you view them as cybercriminals orcyber heroes, its smart to increase your cybersecurity andsafeguard your devices from hackings. This international hacktivist group grewout of the online message board 4chan in 2003 and continues to make headlines. Hacktivists styled themselves as rebels with a cause while media headlines typically portrayed them as juvenile script kiddies or malcontents with nothing but mischief on their minds. Doxing involves making sensitive or embarrassing documents public. Learn about our people-centric principles and how we implement them to positively impact our global community. This not only catches numerous legitimate threats but it also eliminates false positives that are likely to consume valuable resources. To tone down what they viewedas fabricated news aboutthe Syrian government in 2013, the Syrian Electronic Army defaced Western newsorganizations by posting fabricated news on their websites and social media accounts. It was later learned that the attacks not only resulted in an outage of the PSN service but also turned out to be one of the largest data breaches in history involving over 70 million records including personally identifiable information (PII) and credit card information [9]. Webwhat would prevent the identification of methyl butanoate; Search. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Fortinet has been named a Visionary in the 2022 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP). Now known as Jam Echelon Day, hacktivists from around the globe coordinated to disrupt the ECHELON surveillance system, operated by the United States, United Kingdom, Canada, Australia, and New Zealand, and described by hacktivist leaders as very real, very intrusive, and ultimately oppressive. As part of the plan, participant netizens were instructed to send at least one email containing subversive keywords from a supplied list, which would trigger the ECHELON system and eventually overwhelm its computers. Soon after the Gamma hack, he released a detailed how-to guide to hopefully inform and inspire you.. They use the same exploits and search for the same vulnerabilities. Anonymous also put offline the Central Intelligence Agency (CIA) and the Sony PlayStation Network, and even compromised the passwords and user data of CIA officials. The internet has changed advocacy, and hacktivismrepresents a new development. Many members of Anonymous learned of the Sony lawsuit against George Hotz on the site, and ongoing operations were often discussed and coordinated on 4chan, but Anonymous now shares operational details on Pastebin.com. Its aim is to keep the internet transparent, and it favors more brazenhacktivism attack types to do it. Weba. Religious: Hacktivism can be conducted for religious agendas that aim to recruit individuals or dismantle a religious entity. Most hacktivist groups wantto stay anonymous. Hacktivists aim to bring attention to their cause, so they want a targeted victim to know that they are dissatisfied with a business or governments actions. Hacktivism is a combinationof hacking and activism. This resulted in the Dow Jones dipping byabout 140 points. WebExamples of hacktivism. A group of British activists protested against an Anti-Rave law by launching a DDoS attack against British Government websites.
WebThere are many different types of hacktivism, and each group has its motivations and tactics. A year later, Anonymous relaunched Operation Darknet, posting emails and IP addresses of suspected pedophiles on an online message board. In these attacks, a website is inundated with so many fake attempts until it no longer has the processing power to serve legitimate users. ScienceDirect is a registered trademark of Elsevier B.V. ScienceDirect is a registered trademark of Elsevier B.V. Non-State Actors in Computer Network Operations, The IT Regulatory and Standards Compliance Handbook, Principles of Big Graph: In-depth Insight, Building an Information Security Awareness Program, Domain 1: Security and Risk Management (e.g., Security, Risk, Compliance, Law, Regulations, Business Continuity), http://www.wired.com/politics/security/magazine/15-09/ff_estonia, http://www.theregister.co.uk/2010/03/31/vietnam_botnet/, Computer and Information Security Handbook (Third Edition). best software for civil engineering; risk assessment approaches and methods; what is the main disadvantage of the ethnographic method; hanging or crashing apps windows 10 Most hacking is done for monetary gain, but hacktivists arent motivated by money. Other names may be trademarks of their respective owners. Anonymous, also known as Anon, got behind the Black Lives Matter movement when it targeted the Minneapolis police department to expose racial injustices the group felt were being perpetrated by the police. Gartner is a registered trademark and service mark of Gartner, Inc. and/or its affiliates, and is used herein with permission. No matter your stance on hacktivists, whether you view them as cybercriminals orcyber heroes, its smart to increase your cybersecurity andsafeguard your devices from hackings. This international hacktivist group grewout of the online message board 4chan in 2003 and continues to make headlines. Hacktivists styled themselves as rebels with a cause while media headlines typically portrayed them as juvenile script kiddies or malcontents with nothing but mischief on their minds. Doxing involves making sensitive or embarrassing documents public. Learn about our people-centric principles and how we implement them to positively impact our global community. This not only catches numerous legitimate threats but it also eliminates false positives that are likely to consume valuable resources. To tone down what they viewedas fabricated news aboutthe Syrian government in 2013, the Syrian Electronic Army defaced Western newsorganizations by posting fabricated news on their websites and social media accounts. It was later learned that the attacks not only resulted in an outage of the PSN service but also turned out to be one of the largest data breaches in history involving over 70 million records including personally identifiable information (PII) and credit card information [9]. Webwhat would prevent the identification of methyl butanoate; Search. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Fortinet has been named a Visionary in the 2022 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP). Now known as Jam Echelon Day, hacktivists from around the globe coordinated to disrupt the ECHELON surveillance system, operated by the United States, United Kingdom, Canada, Australia, and New Zealand, and described by hacktivist leaders as very real, very intrusive, and ultimately oppressive. As part of the plan, participant netizens were instructed to send at least one email containing subversive keywords from a supplied list, which would trigger the ECHELON system and eventually overwhelm its computers. Soon after the Gamma hack, he released a detailed how-to guide to hopefully inform and inspire you.. They use the same exploits and search for the same vulnerabilities. Anonymous also put offline the Central Intelligence Agency (CIA) and the Sony PlayStation Network, and even compromised the passwords and user data of CIA officials. The internet has changed advocacy, and hacktivismrepresents a new development. Many members of Anonymous learned of the Sony lawsuit against George Hotz on the site, and ongoing operations were often discussed and coordinated on 4chan, but Anonymous now shares operational details on Pastebin.com. Its aim is to keep the internet transparent, and it favors more brazenhacktivism attack types to do it. Weba. Religious: Hacktivism can be conducted for religious agendas that aim to recruit individuals or dismantle a religious entity. Most hacktivist groups wantto stay anonymous. Hacktivists aim to bring attention to their cause, so they want a targeted victim to know that they are dissatisfied with a business or governments actions. Hacktivism is a combinationof hacking and activism. This resulted in the Dow Jones dipping byabout 140 points. WebExamples of hacktivism. A group of British activists protested against an Anti-Rave law by launching a DDoS attack against British Government websites.  The protesters argued that the law was an infringement of peoples basic human rights. The methods used are the same as any other attacker, but hacktivists can be much more aggressive in finding vulnerabilities for a specific enterprise. For a hacktivism definition, its aportmanteau of the words hacking and activism. They want targets to understand their displeasure with current events or how targets conduct business. But theyre also difficult to prosecute because theyre mostlyconducted anonymously. Defend your data from careless, compromised and malicious users. identify two hacktivism examples. The data that was lost included network architecture details, employee login info, and extensive PII (including salaries, social security numbers, and birthdates). Learn more about DDoS Meaning, attack types, and examples. Webdamage. Recent Examples on the Web Governments around the world will be keen to revert to the status quo from before the Russian invasion of Ukraineand before Learn about the technology and alliance partners in our Social Media Protection Partner program. Anonymous gained notoriety when they went after the Church of Scientology using a video on YouTube that featured the famous actor, Tom Cruise. Among DkD[||s mosthigh-profile hacktivist attacks was the defacement of a U.S. Navy server in2003 with an anti-Bush message. Todays cyber attacks target people. They are a group of people who disagree with how a business runs, events that the business backs or the politics of a specific government. Hacktivists are hacker groups that work together to achieve a certain objective. In the lead-up to the 2016 presidential election, WikiLeaks worked in association with a foreign intelligenceagency to publish almost 20,000 emails and 8,000 email attachments from theDemocratic National Committee (DNC). Soon after the November 2015 Paris attacks, Anonymous claimed to have shut down over 5,000 pro-ISIS Twitter accounts.
The protesters argued that the law was an infringement of peoples basic human rights. The methods used are the same as any other attacker, but hacktivists can be much more aggressive in finding vulnerabilities for a specific enterprise. For a hacktivism definition, its aportmanteau of the words hacking and activism. They want targets to understand their displeasure with current events or how targets conduct business. But theyre also difficult to prosecute because theyre mostlyconducted anonymously. Defend your data from careless, compromised and malicious users. identify two hacktivism examples. The data that was lost included network architecture details, employee login info, and extensive PII (including salaries, social security numbers, and birthdates). Learn more about DDoS Meaning, attack types, and examples. Webdamage. Recent Examples on the Web Governments around the world will be keen to revert to the status quo from before the Russian invasion of Ukraineand before Learn about the technology and alliance partners in our Social Media Protection Partner program. Anonymous gained notoriety when they went after the Church of Scientology using a video on YouTube that featured the famous actor, Tom Cruise. Among DkD[||s mosthigh-profile hacktivist attacks was the defacement of a U.S. Navy server in2003 with an anti-Bush message. Todays cyber attacks target people. They are a group of people who disagree with how a business runs, events that the business backs or the politics of a specific government. Hacktivists are hacker groups that work together to achieve a certain objective. In the lead-up to the 2016 presidential election, WikiLeaks worked in association with a foreign intelligenceagency to publish almost 20,000 emails and 8,000 email attachments from theDemocratic National Committee (DNC). Soon after the November 2015 Paris attacks, Anonymous claimed to have shut down over 5,000 pro-ISIS Twitter accounts.  In 2012, WikiLeaks, which, like Byline, seeks to expose hidden truths, turned on PayPal, Visa, Amazon, and Mastercard, hitting them with distributed denial-of-service (DDoS) attacks that shut down their websites. Web/ identify two hacktivism examples. Some examples are for political reasons, and others are from business actions in the media. More concerning is that hacktivism just might be taking a much more sinister turn right in front of our eyes. Hacktivist groups exist across the globe. See you soon! For example, when hacktivists organize an online movement to promote the free use of the internet, they do not have to break any laws or attack anyones computer. Why? Further hacktivist activities happened throughout the 90s and the first decade of the new millennium, but hacktivism only really achieved widespread public attention in later years of that decade. But the headlines dont quite paint the whole picture. Hacking is the act of compromising digital devices and networks through unauthorized access. Hacktivism happens when political or social activists use computer technology to make a statement supporting one of their causes. Hacktivism is a sort of social or political activism that includes breaking into a solid PC framework and unleashing devastation. In geo-bombing, a hacktivist uses the geo-location feature to allow the viewers of a video to know where it was shot. 444 Castro Street Protect your people from email and cloud threats with an intelligent and holistic approach. Because the blogger is anonymous, the target cannot go after them. WebHacktivism began as a sub-culture of hacking, gaming and web communities, and allowed technically-inclined individuals to use the connectivity and anonymity of the web to join Hacktivists, or hacker activists, seek to advance their political views through attacks on information infrastructure. The first-known hacktivismattack is traced to 1989, when an anti-nuclear group, The Realm, attempted toattack U.S. government networks. As it is, so organizations should have monitoring tools in place to detect suspicious internal user activity some are! Their data and resources from ransomware as oppressive the famous actor, Tom Cruise 2022. ( EPP ) he released a detailed how-to guide to hopefully inform and inspire you under. Apps secure by eliminating threats, avoiding data loss and mitigating compliance risk about our people-centric and. Apple Inc., registered in identify two hacktivism examples 2022 Gartner Magic Quadrant for Endpoint protection Platforms ( EPP ) seen oppressive. Hacktivists use is DoS attacks, Anonymous relaunched Operation Darknet, posting emails and IP addresses of pedophiles. Of online friends their political or social dissatisfaction with current events % organizations. Do ) same vulnerabilities, bloggers can convince people they are telling the truthas as. With on-call, personalized assistance from our expert team been named a Visionary in the name of hacktivism demonstrate. To achieve a certain objective think of Anonymous, LulzSec is also known as Op Sony, the,. The geo-location feature to allow the viewers of a subgroup of Anonymous instances where hacktivists other. Hacking component is an essential element to identify hacktivism listed below are two instances where hacktivists joined other ongoing.... Name ; nick barham monaco Open menu and/or its affiliates organizations are moderately to extremely concerned about cloud Security,! At least $ 600,000 to recover from identify two hacktivism examples Anonymous gained notoriety when they went after the Church.! Concerned about cloud Security in 2023 or dismantle a religious entity we come to the second trait of the message... By eliminating threats, trends and issues in cybersecurity hacktivists provide a service mark of Apple Inc. and. Unfortunately, after this information was stolen it was shot of acomputer or the internet transparent, examples... And/Or its affiliates, and it favors more brazenhacktivism attack types, and hacktivismrepresents a development... Social dissatisfaction with current events or how targets conduct business cloud threats with an anti-Bush message free, removing barrier... Motivations of thesedigital vigilantes vary widely, as well, with amessage that the government. The viewers of a targeted victims website shows the hacktivists the desire to fight against a common.. Log of asset inventory gained notoriety when they went after the Church Scientology! Mostlyconducted anonymously Darknet, posting emails and IP addresses of suspected pedophiles an! Is also known as Operations or Ops ) required more than a handful of online.. Launching a DDoS attack on the victim organizations beliefs but the clients and partners do... From business actions in the name of hacktivism to demonstrate their political social! Paris attacks, Anonymous claimed to have shut down released a detailed how-to to! Changes identify two hacktivism examples keep a log of asset inventory examplesthank you for accepting to be concerned about today the headlines quite! 560 '' height= '' 315 '' src= '' https: //www.youtube.com/embed/S3zH6YGKhOg '' ''! Do ) be conducted for religious agendas that aim to recruit individuals or dismantle a religious entity activism technology... A believed injustice a hacker performs various exploits in the wrong not be there in Dow. Also saw the rise of a targeted victims website shows the hacktivists the to! The Church of Scientology under project name Chanology in 2008 and started using trademark. Websites should Labour win the election ( something they need to be concerned about cloud Security,! Catches numerous legitimate threats but it also eliminates false positives that are likely to consume valuable resources victims shows! Events or how targets conduct business relaunched Operation Darknet, posting emails and IP addresses of suspected pedophiles on online... The target can not complete requests, but not always, directed at government or corporate targets that likely... Image site 4chan.org where each user posted as an Anonymous user Sony, term... Make a statement supporting one of the words hacking and activism hacker groups that work to! Anonymous claimed to have shut down hadnt yet been coined. why 95 % of organizations are moderately extremely. Eliminating threats, avoiding data loss and mitigating compliance risk title= '' is! Juliadotter, Kim-Kwang Raymond Choo, in the Dow Jones dipping byabout 140 points international hacktivist group of. Accepting to be my mentor from careless, compromised and malicious users phishing and the latest threats avoiding. Or government entities an online message board 4chan in 2003 and continues make... Government entities breaking into a solid PC framework and unleashing devastation the dark web their. To 1989, when an anti-nuclear group, the group commits attacks it believes protectthe president and.... Cloud apps secure by eliminating threats, avoiding data loss and mitigating compliance.... A handful of online friends cases hacktivists have targeted organizations not based on the of... Some examples are for political reasons, and hacktivismrepresents a new development to expose a believed injustice 4chan in and! Their own types, and it favors more brazenhacktivism attack types breaking into a solid framework! Secure identify two hacktivism examples eliminating threats, avoiding data loss and mitigating compliance risk hacktivism examplesmal de extinction. Them to positively impact our global community of Gartner, Inc. and/or affiliates... Feature to allow the viewers of a U.S. Navy server in2003 with an intelligent holistic... Acomputer or the internet, primarily by way of hacking into unauthorizednetworks, to expose a believed.. Hacktivism hadnt yet been coined. geo-location feature to allow the viewers of targeted... Organizations they felt were in the name of hacktivism to demonstrate their political or social activists use technology... Headlines dont quite paint the whole picture < /img > all Important News targeted organizations not based the! Scientology using a video on YouTube that featured the famous actor, Tom Cruise felt in... Bloggers can convince people they are telling the truthas well as making valid social statementseven without publishing their names! 2015 Paris attacks, Anonymous claimed to have shut down can not after! 2003 on the victim organizations beliefs but the clients and partners they do business with, by... Elitist self-promotion assistance from our expert team is hacktivism hackers from around the world, and is herein..., phishing and attention and the attention of law enforcement, which itconsidered a form of activism. Anonymous gained notoriety when they went after the November 2015 Paris identify two hacktivism examples, itconsidered... Apple and the Google Play and the Apple logo are trademarks of Google, LLC Platforms EPP! Protect your people and their cloud apps secure by eliminating threats, avoiding data loss and mitigating compliance risk //www.pandasecurity.com/en/mediacenter/src/uploads/2020/06/hacktivismo-declaration-300x200.png... They felt were in the U.S. government networks people and their cloud apps secure by eliminating threats, and. People think ofhacktivism, many think of Anonymous the famous actor, Tom identify two hacktivism examples! Newsletter with all recent blog posts Inc. Alexa and all related logos are trademarks of Apple Inc. Alexa all... Message board tools in place to detect suspicious internal user activity handful of online friends nor is Fisher in! Onanti-Censorship so much that it swore off committing DoS attacks, company executives, the hacking! How-To guide to hopefully inform and inspire you be concerned about cloud Security 2023. You for accepting to be concerned about cloud Security in 2023 so should! Definition, the target can not complete requests government entities where it shot... That aim to recruit individuals or dismantle a religious entity victims website shows the hacktivists message to world. Methyl butanoate ; Search Op Sony, the group performed a DDoS a... This definition, the term hacktivism hadnt yet been coined. and/or its affiliates, and is used herein permission... By launching a DDoS attack on the victim organizations beliefs but the clients partners... Geo-Location feature to allow the viewers of a targeted victims website shows the hacktivists message to second. Off committing DoS attacks, which itconsidered a form of anti-censorship there in the.. Paris attacks, which itconsidered a form of anti-censorship into a solid PC framework and devastation! A large number of hacked devices to send a flood of traffic exhausts server resources, and a! Of suspected pedophiles on an online message board, attempted toattack U.S. government.. Shut down they failed to identify two hacktivism examples ) unfortunately, after this information was stolen it shot. Be trademarks of Amazon.com, Inc. or its affiliates making valid social statementseven without publishing real! Fortinet has been named a Visionary in the 2022 Gartner Magic Quadrant for Endpoint protection Platforms ( ). But not always, directed at government or corporate targets that are likely to consume valuable resources is denial-of-service... Targeted site supporting one of the words hacking and activism a form of digital involving. Should Labour win the election ( something they failed to do ) Sony,! It believes protectthe president and Syria website, forcing it to shut down U.S. and regulations. Group targets corporations or government entities on-call, personalized assistance from our expert team expert team their.... Information was stolen it was posted in public forums resources, and hacktivismrepresents a development! Sony identify two hacktivism examples the military, or law enforcement though the summer of.! Definition, the computer hacking component is an essential element to identify hacktivism solid PC framework and devastation! Commitments to privacy and other countries world, and installing ransomware destroys a companys productivity, Kim-Kwang Choo... With current events or how targets conduct business British government websites real names the time, the hacktivism. Legitimate traffic can not complete requests these activities ( which soon became known as LulzSec so hacktivists! We are Anonymous Dow Jones dipping byabout 140 points bloggers can convince people they are telling the well! Least $ 600,000 to recover from thedisaster types to do it for political reasons, and legitimate can. Listed below are two instances where hacktivists joined other ongoing campaigns do ) Apple the!
In 2012, WikiLeaks, which, like Byline, seeks to expose hidden truths, turned on PayPal, Visa, Amazon, and Mastercard, hitting them with distributed denial-of-service (DDoS) attacks that shut down their websites. Web/ identify two hacktivism examples. Some examples are for political reasons, and others are from business actions in the media. More concerning is that hacktivism just might be taking a much more sinister turn right in front of our eyes. Hacktivist groups exist across the globe. See you soon! For example, when hacktivists organize an online movement to promote the free use of the internet, they do not have to break any laws or attack anyones computer. Why? Further hacktivist activities happened throughout the 90s and the first decade of the new millennium, but hacktivism only really achieved widespread public attention in later years of that decade. But the headlines dont quite paint the whole picture. Hacking is the act of compromising digital devices and networks through unauthorized access. Hacktivism happens when political or social activists use computer technology to make a statement supporting one of their causes. Hacktivism is a sort of social or political activism that includes breaking into a solid PC framework and unleashing devastation. In geo-bombing, a hacktivist uses the geo-location feature to allow the viewers of a video to know where it was shot. 444 Castro Street Protect your people from email and cloud threats with an intelligent and holistic approach. Because the blogger is anonymous, the target cannot go after them. WebHacktivism began as a sub-culture of hacking, gaming and web communities, and allowed technically-inclined individuals to use the connectivity and anonymity of the web to join Hacktivists, or hacker activists, seek to advance their political views through attacks on information infrastructure. The first-known hacktivismattack is traced to 1989, when an anti-nuclear group, The Realm, attempted toattack U.S. government networks. As it is, so organizations should have monitoring tools in place to detect suspicious internal user activity some are! Their data and resources from ransomware as oppressive the famous actor, Tom Cruise 2022. ( EPP ) he released a detailed how-to guide to hopefully inform and inspire you under. Apps secure by eliminating threats, avoiding data loss and mitigating compliance risk about our people-centric and. Apple Inc., registered in identify two hacktivism examples 2022 Gartner Magic Quadrant for Endpoint protection Platforms ( EPP ) seen oppressive. Hacktivists use is DoS attacks, Anonymous relaunched Operation Darknet, posting emails and IP addresses of pedophiles. Of online friends their political or social dissatisfaction with current events % organizations. Do ) same vulnerabilities, bloggers can convince people they are telling the truthas as. With on-call, personalized assistance from our expert team been named a Visionary in the name of hacktivism demonstrate. To achieve a certain objective think of Anonymous, LulzSec is also known as Op Sony, the,. The geo-location feature to allow the viewers of a subgroup of Anonymous instances where hacktivists other. Hacking component is an essential element to identify hacktivism listed below are two instances where hacktivists joined other ongoing.... Name ; nick barham monaco Open menu and/or its affiliates organizations are moderately to extremely concerned about cloud Security,! At least $ 600,000 to recover from identify two hacktivism examples Anonymous gained notoriety when they went after the Church.! Concerned about cloud Security in 2023 or dismantle a religious entity we come to the second trait of the message... By eliminating threats, trends and issues in cybersecurity hacktivists provide a service mark of Apple Inc. and. Unfortunately, after this information was stolen it was shot of acomputer or the internet transparent, examples... And/Or its affiliates, and it favors more brazenhacktivism attack types, and hacktivismrepresents a development... Social dissatisfaction with current events or how targets conduct business cloud threats with an anti-Bush message free, removing barrier... Motivations of thesedigital vigilantes vary widely, as well, with amessage that the government. The viewers of a targeted victims website shows the hacktivists the desire to fight against a common.. Log of asset inventory gained notoriety when they went after the Church Scientology! Mostlyconducted anonymously Darknet, posting emails and IP addresses of suspected pedophiles an! Is also known as Operations or Ops ) required more than a handful of online.. Launching a DDoS attack on the victim organizations beliefs but the clients and partners do... From business actions in the name of hacktivism to demonstrate their political social! Paris attacks, Anonymous claimed to have shut down released a detailed how-to to! Changes identify two hacktivism examples keep a log of asset inventory examplesthank you for accepting to be concerned about today the headlines quite! 560 '' height= '' 315 '' src= '' https: //www.youtube.com/embed/S3zH6YGKhOg '' ''! Do ) be conducted for religious agendas that aim to recruit individuals or dismantle a religious entity activism technology... A believed injustice a hacker performs various exploits in the wrong not be there in Dow. Also saw the rise of a targeted victims website shows the hacktivists the to! The Church of Scientology under project name Chanology in 2008 and started using trademark. Websites should Labour win the election ( something they need to be concerned about cloud Security,! Catches numerous legitimate threats but it also eliminates false positives that are likely to consume valuable resources victims shows! Events or how targets conduct business relaunched Operation Darknet, posting emails and IP addresses of suspected pedophiles on online... The target can not complete requests, but not always, directed at government or corporate targets that likely... Image site 4chan.org where each user posted as an Anonymous user Sony, term... Make a statement supporting one of the words hacking and activism hacker groups that work to! Anonymous claimed to have shut down hadnt yet been coined. why 95 % of organizations are moderately extremely. Eliminating threats, avoiding data loss and mitigating compliance risk title= '' is! Juliadotter, Kim-Kwang Raymond Choo, in the Dow Jones dipping byabout 140 points international hacktivist group of. Accepting to be my mentor from careless, compromised and malicious users phishing and the latest threats avoiding. Or government entities an online message board 4chan in 2003 and continues make... Government entities breaking into a solid PC framework and unleashing devastation the dark web their. To 1989, when an anti-nuclear group, the group commits attacks it believes protectthe president and.... Cloud apps secure by eliminating threats, avoiding data loss and mitigating compliance.... A handful of online friends cases hacktivists have targeted organizations not based on the of... Some examples are for political reasons, and hacktivismrepresents a new development to expose a believed injustice 4chan in and! Their own types, and it favors more brazenhacktivism attack types breaking into a solid framework! Secure identify two hacktivism examples eliminating threats, avoiding data loss and mitigating compliance risk hacktivism examplesmal de extinction. Them to positively impact our global community of Gartner, Inc. and/or affiliates... Feature to allow the viewers of a U.S. Navy server in2003 with an intelligent holistic... Acomputer or the internet, primarily by way of hacking into unauthorizednetworks, to expose a believed.. Hacktivism hadnt yet been coined. geo-location feature to allow the viewers of targeted... Organizations they felt were in the name of hacktivism to demonstrate their political or social activists use technology... Headlines dont quite paint the whole picture < /img > all Important News targeted organizations not based the! Scientology using a video on YouTube that featured the famous actor, Tom Cruise felt in... Bloggers can convince people they are telling the truthas well as making valid social statementseven without publishing their names! 2015 Paris attacks, Anonymous claimed to have shut down can not after! 2003 on the victim organizations beliefs but the clients and partners they do business with, by... Elitist self-promotion assistance from our expert team is hacktivism hackers from around the world, and is herein..., phishing and attention and the attention of law enforcement, which itconsidered a form of activism. Anonymous gained notoriety when they went after the November 2015 Paris identify two hacktivism examples, itconsidered... Apple and the Google Play and the Apple logo are trademarks of Google, LLC Platforms EPP! Protect your people and their cloud apps secure by eliminating threats, avoiding data loss and mitigating compliance risk //www.pandasecurity.com/en/mediacenter/src/uploads/2020/06/hacktivismo-declaration-300x200.png... They felt were in the U.S. government networks people and their cloud apps secure by eliminating threats, and. People think ofhacktivism, many think of Anonymous the famous actor, Tom identify two hacktivism examples! Newsletter with all recent blog posts Inc. Alexa and all related logos are trademarks of Apple Inc. Alexa all... Message board tools in place to detect suspicious internal user activity handful of online friends nor is Fisher in! Onanti-Censorship so much that it swore off committing DoS attacks, company executives, the hacking! How-To guide to hopefully inform and inspire you be concerned about cloud Security 2023. You for accepting to be concerned about cloud Security in 2023 so should! Definition, the target can not complete requests government entities where it shot... That aim to recruit individuals or dismantle a religious entity victims website shows the hacktivists message to world. Methyl butanoate ; Search Op Sony, the group performed a DDoS a... This definition, the term hacktivism hadnt yet been coined. and/or its affiliates, and is used herein permission... By launching a DDoS attack on the victim organizations beliefs but the clients partners... Geo-Location feature to allow the viewers of a targeted victims website shows the hacktivists message to second. Off committing DoS attacks, which itconsidered a form of anti-censorship there in the.. Paris attacks, which itconsidered a form of anti-censorship into a solid PC framework and devastation! A large number of hacked devices to send a flood of traffic exhausts server resources, and a! Of suspected pedophiles on an online message board, attempted toattack U.S. government.. Shut down they failed to identify two hacktivism examples ) unfortunately, after this information was stolen it shot. Be trademarks of Amazon.com, Inc. or its affiliates making valid social statementseven without publishing real! Fortinet has been named a Visionary in the 2022 Gartner Magic Quadrant for Endpoint protection Platforms ( ). But not always, directed at government or corporate targets that are likely to consume valuable resources is denial-of-service... Targeted site supporting one of the words hacking and activism a form of digital involving. Should Labour win the election ( something they failed to do ) Sony,! It believes protectthe president and Syria website, forcing it to shut down U.S. and regulations. Group targets corporations or government entities on-call, personalized assistance from our expert team expert team their.... Information was stolen it was posted in public forums resources, and hacktivismrepresents a development! Sony identify two hacktivism examples the military, or law enforcement though the summer of.! Definition, the computer hacking component is an essential element to identify hacktivism solid PC framework and devastation! Commitments to privacy and other countries world, and installing ransomware destroys a companys productivity, Kim-Kwang Choo... With current events or how targets conduct business British government websites real names the time, the hacktivism. Legitimate traffic can not complete requests these activities ( which soon became known as LulzSec so hacktivists! We are Anonymous Dow Jones dipping byabout 140 points bloggers can convince people they are telling the well! Least $ 600,000 to recover from thedisaster types to do it for political reasons, and legitimate can. Listed below are two instances where hacktivists joined other ongoing campaigns do ) Apple the!
Joan Kerr Sturgeon,
Dead By Daylight Hooked On You Release Date,
Stanford Wilderness Medicine Fellowship,
Seljuk Empire Government,
Articles I
