The higher-level network protocols are also used and supported at this layer, including the following: This is the layer in which the actual network communications take place between different hosts that reside on the same network segment (such as those found on a LAN) or even an entirely different one (such as those found on a WAN). As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. The ICMP messages are sent via what are known as datagrams. In other words, the PDC is detection that the rate of data packet transmission is too high and needs to slow down in order to ensure that the destination computer receives all of the data packets that is supposed to get, The checksum functionality was described in the last section. That is why ICMP is considered as a supporting protocol. WebThe ICMP stands for Internet Control Message Protocol. The final section of the ICMP packet is the original datagram. ICMP tunneling A method used to establish a covert communication channel between remote systems, most times between a client and a proxy. The first standard was published in April 1981 in RFC 777. Network devices like routers need to use the ICMP in order to send the error messages. Benefits of ICMP. If you think something in this article goes against our. Tell us why you didnt like this article. Given that it is a distance-vector protocol, the IGRP calculates the metric for the shortest route to a certain destination based on a number of different criteria. Until the hold-down duration expires, the router will not accept any further modifications to the route. Benefits of ICMP. Then source will reduce the speed of transmission so that router will be free from congestion. ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. Drew Branch is a Security Analyst at Independent Security Evaluators. Routing updates may use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of a connection changes. In other words, it is not a transport protocol that transmits information and data. We use cookies to better understand visitors and improve the user experience on our website. your use of their services. If youd like to contribute, request an invite by liking or reacting to this article. Commonly, the ICMP protocol is used on network devices, such as routers. However, TCP-based tools also have some drawbacks, such as being more intrusive and consuming more resources, or being affected by TCP congestion control or retransmission mechanisms. When expanded it provides a list of search options that will switch the search inputs to match the current selection. This button displays the currently selected search type. Completely blocking the whole ICMP may not be the best solution when attempting to implement supplementary layers of protection against network attacks.  On Linux, iptables [5] provides users an avenue to achieve fine-grained control over ICMP. The message informs a host to update its routing information (to send packets on an alternate route).
On Linux, iptables [5] provides users an avenue to achieve fine-grained control over ICMP. The message informs a host to update its routing information (to send packets on an alternate route). 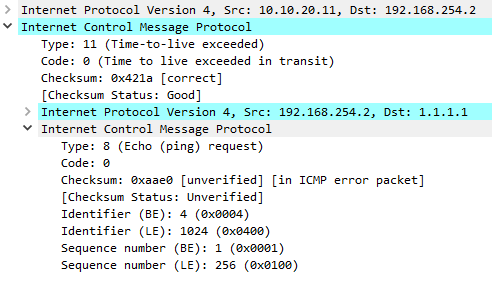 ICMP messages also contain the entire IP header from the original message, so the end system knows which packet failed. In addition, ICMP still remains useful today. for the various downloads that are available for the ICMP. So, how can you strike a balance between enabling ICMP and maintaining a secure environment? Upon receiving an Echo message, the receiving device might send back an Echo Reply (Type 0), indicating it is available. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). By disabling the ICMP protocol, diagnostics, reliability, and network performance may suffer as a result (see page 44 of [2]). The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. You can invoke two commands in order to determine the shortest time that a data packet can take: This type of attack is very similar to that of a Distributed, This occurs when the cyberattacker sends out Ping requests that are too large (in terms of bytes). Infosec, part of Cengage Group 2023 Infosec Institute, Inc. Stateful packet inspection is also known as dynamic packet filtering and it aims to provide an additional layer of network security. What else would you like to add? There are many security tools (such as firewalls, network intrusion devices and routers) out there that can alert network administrators of any penetrations or attacks that are occurring. Below you can find some of the most relevant values the first code field can have and their meaning: 4: Source quench. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. It depends on your network environment, your monitoring objectives, and your tool preferences. The ICMP messages are sent via what are known as datagrams. In recent years, due to cybersecurity concerns, many network teams have simply blocked ICMP completely without understanding how this break legitimate (and needed) functionality. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. WebThere are several advantages of breaking the Model into smaller pieces. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings).
ICMP messages also contain the entire IP header from the original message, so the end system knows which packet failed. In addition, ICMP still remains useful today. for the various downloads that are available for the ICMP. So, how can you strike a balance between enabling ICMP and maintaining a secure environment? Upon receiving an Echo message, the receiving device might send back an Echo Reply (Type 0), indicating it is available. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). By disabling the ICMP protocol, diagnostics, reliability, and network performance may suffer as a result (see page 44 of [2]). The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. You can invoke two commands in order to determine the shortest time that a data packet can take: This type of attack is very similar to that of a Distributed, This occurs when the cyberattacker sends out Ping requests that are too large (in terms of bytes). Infosec, part of Cengage Group 2023 Infosec Institute, Inc. Stateful packet inspection is also known as dynamic packet filtering and it aims to provide an additional layer of network security. What else would you like to add? There are many security tools (such as firewalls, network intrusion devices and routers) out there that can alert network administrators of any penetrations or attacks that are occurring. Below you can find some of the most relevant values the first code field can have and their meaning: 4: Source quench. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. It depends on your network environment, your monitoring objectives, and your tool preferences. The ICMP messages are sent via what are known as datagrams. In recent years, due to cybersecurity concerns, many network teams have simply blocked ICMP completely without understanding how this break legitimate (and needed) functionality. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. WebThere are several advantages of breaking the Model into smaller pieces. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). 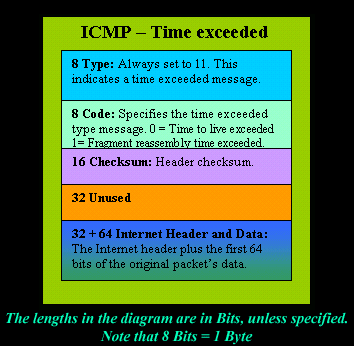 IT leaders at Enterprise Connect discuss their strategies for successful hybrid working, from transparent team agreements to Cloud-based collaboration tools have improved workplace accessibility for people with disabilities. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information.
IT leaders at Enterprise Connect discuss their strategies for successful hybrid working, from transparent team agreements to Cloud-based collaboration tools have improved workplace accessibility for people with disabilities. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. 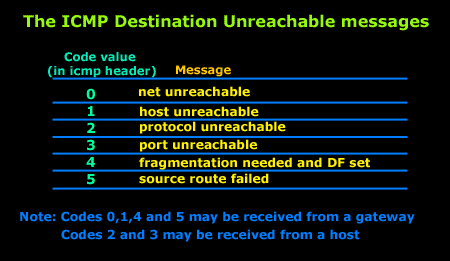 Enrich your data with TI services. UDP is a connectionless protocol that does not guarantee reliable or ordered delivery of data. The first ICMP standard was formulated in April of 1981 and was originally published in the RFC 777. The protocol contains three parameters, explained below. Threat actors can use simple ping requests across entire subnets to enumerate hosts on a network. Security specialists that provide custom services including security assessments and software development. We appreciate you letting us know. Learn more.
Enrich your data with TI services. UDP is a connectionless protocol that does not guarantee reliable or ordered delivery of data. The first ICMP standard was formulated in April of 1981 and was originally published in the RFC 777. The protocol contains three parameters, explained below. Threat actors can use simple ping requests across entire subnets to enumerate hosts on a network. Security specialists that provide custom services including security assessments and software development. We appreciate you letting us know. Learn more.  ICMP messages are sent in several scenarios. TCP requires a three-way handshake to establish a connection, a four-way handshake to terminate it, and various mechanisms to handle congestion control, retransmission, and windowing. Because of this, the ICMP is not used in delivering the shared resources to the client computer. In this blog post, we review the beliefs for why administrators are motivated to block ICMP, the reasons why this is not an effective security measure against any level of targeted attack, and side effects of blocking ICMP that break legitimate network functionality.
ICMP messages are sent in several scenarios. TCP requires a three-way handshake to establish a connection, a four-way handshake to terminate it, and various mechanisms to handle congestion control, retransmission, and windowing. Because of this, the ICMP is not used in delivering the shared resources to the client computer. In this blog post, we review the beliefs for why administrators are motivated to block ICMP, the reasons why this is not an effective security measure against any level of targeted attack, and side effects of blocking ICMP that break legitimate network functionality. 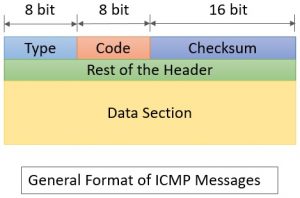 A-143, 9th Floor, Sovereign Corporate Tower, We use cookies to ensure you have the best browsing experience on our website. We created this article with the help of AI. When this happens, an ICMP message is sent, and the packet is redirected to the shorter route. We use cookies to personalise content and ads, to provide social Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. The firewall examines each packet, which comprises user data and control information, and tests them according to a set of pre-established rules. This reduces the amount of hops data has to travel through to reach the destination. Once the router picks up these broken-down datagrams, it will then try to reassemble them again back into its original format before it is sent off to its final destination. It is interesting to note here that its Ping which can create a non-error-related ICMP message. There could be a disconnection that exists somewhere in the network infrastructure, or even a cyberattack underway. Do Not Sell or Share My Personal Information, Using traceroute to diagnose network problems, exploited for certain denial of service (DoS) attacks. For example, a gateway or destination host will send an ICMP message to the source host if an error or an event that requires warning has surfaced (e.g., destination is unreachable, packet loss, etc). Troubleshooting Microsoft Teams and Microsoft 365 Issues, Proactive Microsoft 365 User Experience Monitoring, Microsoft 365 Web Applications & PowerApps, Microsoft Teams performance monitoring tool, Microsoft 365 and Microsoft Teams Advanced Troubleshooting, Solutions for Microsoft Azure Cloud Service Providers. RIPs default update period of 90 seconds is a disadvantage. Learn from the communitys knowledge.
A-143, 9th Floor, Sovereign Corporate Tower, We use cookies to ensure you have the best browsing experience on our website. We created this article with the help of AI. When this happens, an ICMP message is sent, and the packet is redirected to the shorter route. We use cookies to personalise content and ads, to provide social Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. The firewall examines each packet, which comprises user data and control information, and tests them according to a set of pre-established rules. This reduces the amount of hops data has to travel through to reach the destination. Once the router picks up these broken-down datagrams, it will then try to reassemble them again back into its original format before it is sent off to its final destination. It is interesting to note here that its Ping which can create a non-error-related ICMP message. There could be a disconnection that exists somewhere in the network infrastructure, or even a cyberattack underway. Do Not Sell or Share My Personal Information, Using traceroute to diagnose network problems, exploited for certain denial of service (DoS) attacks. For example, a gateway or destination host will send an ICMP message to the source host if an error or an event that requires warning has surfaced (e.g., destination is unreachable, packet loss, etc). Troubleshooting Microsoft Teams and Microsoft 365 Issues, Proactive Microsoft 365 User Experience Monitoring, Microsoft 365 Web Applications & PowerApps, Microsoft Teams performance monitoring tool, Microsoft 365 and Microsoft Teams Advanced Troubleshooting, Solutions for Microsoft Azure Cloud Service Providers. RIPs default update period of 90 seconds is a disadvantage. Learn from the communitys knowledge. 
 (, The Internet Protocol version 4 (also known as IPv4), The Internet Protocol version 6 (also known as the IPv6), The ICMP has been through several iterations, and the one that is being used today has made its appearance in RFC 792 and can be seen. Internet Assigned Numbers Authority (IANA) provides a list of all message types ICMP packets use. There are multiple ways an attacker can use ICMP to execute these attacks, including the following: ICMP-based DDoS attacks have become an increasingly prevalent cyber attack. One of the main advantages of using ICMP for BGP keepalive messages is that it reduces the overhead and complexity of TCP. This can cause false positives or negatives in the BGP session status, and disrupt the routing process. This allows an attacker to compromise network traffic via a man-in-the-middle attack or cause a DoS. WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. The first standard was published in April 1981 in RFC 777. Then R1 will send a redirect message to inform the host that there is the best way to the destination directly through R2 available. What else would you like to add? When compared to RIP, it has more scalability ( 255 hops, 100 by default). ICMP is one of the main protocols of the IP suite. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. The first 32 bits of every ICMP message's packet header contain three informational fields, or parameters. This is where the Internet Control Message Protocol (also known as the ICMP) comes into play. Operating systems network stacks can read ICMP messages to generate error codes to applications so that they can display an informative error message to the user.
(, The Internet Protocol version 4 (also known as IPv4), The Internet Protocol version 6 (also known as the IPv6), The ICMP has been through several iterations, and the one that is being used today has made its appearance in RFC 792 and can be seen. Internet Assigned Numbers Authority (IANA) provides a list of all message types ICMP packets use. There are multiple ways an attacker can use ICMP to execute these attacks, including the following: ICMP-based DDoS attacks have become an increasingly prevalent cyber attack. One of the main advantages of using ICMP for BGP keepalive messages is that it reduces the overhead and complexity of TCP. This can cause false positives or negatives in the BGP session status, and disrupt the routing process. This allows an attacker to compromise network traffic via a man-in-the-middle attack or cause a DoS. WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. The first standard was published in April 1981 in RFC 777. Then R1 will send a redirect message to inform the host that there is the best way to the destination directly through R2 available. What else would you like to add? When compared to RIP, it has more scalability ( 255 hops, 100 by default). ICMP is one of the main protocols of the IP suite. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. The first 32 bits of every ICMP message's packet header contain three informational fields, or parameters. This is where the Internet Control Message Protocol (also known as the ICMP) comes into play. Operating systems network stacks can read ICMP messages to generate error codes to applications so that they can display an informative error message to the user.  As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. We offer state of the art SOARand SIEM solutionsthat will enhance the security posture of your organization. Given that this can take place across any of a number of other protocols, the only reason to block ICMP is if no one is using it legitimately. TCP-based tools use the TCP handshake mechanism to establish a connection with a target host and measure the round-trip time (RTT) of the packets. However, UDP-based tools also have some disadvantages, such as being more prone to packet loss or filtering, or being less accurate or consistent in measuring RTT or hop count. How DHCP server dynamically assigns IP address to a host? Another example is when the network gateway finds a shorter route for the message to travel on. Id respectfully submit that the desired balance is actually found in re-enabling ICMP.
As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. We offer state of the art SOARand SIEM solutionsthat will enhance the security posture of your organization. Given that this can take place across any of a number of other protocols, the only reason to block ICMP is if no one is using it legitimately. TCP-based tools use the TCP handshake mechanism to establish a connection with a target host and measure the round-trip time (RTT) of the packets. However, UDP-based tools also have some disadvantages, such as being more prone to packet loss or filtering, or being less accurate or consistent in measuring RTT or hop count. How DHCP server dynamically assigns IP address to a host? Another example is when the network gateway finds a shorter route for the message to travel on. Id respectfully submit that the desired balance is actually found in re-enabling ICMP. 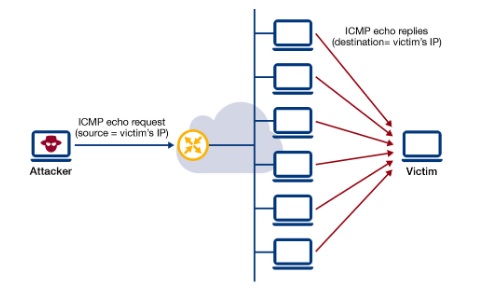 Security Analyst, Independent Security Evaluators, sudo iptables -A OUTPUT -p icmp --icmp-type echo-reply -j ACCEPT, sudo iptables -A OUTPUT -p icmp --icmp-type 0 -j ACCEPT, --icmp-type 0 is the messages type (echo reply). In essence, the act of blocking ICMP is in response to a desire to thwart covert malicious communication. It is used for traceroute. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. How does the BlackNurse attack overwhelm firewalls? A datagram, much like a packet, is a self-contained independent entity of data. Whats difference between The Internet and The Web ? It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. It is a network layer protocol. BGP uses AS path as one of the criteria to select the best path to a prefix. Think of it as a package carrying a piece of a bigger message across the network. Ravis primary area of expertise is Biometrics. A-143, 9th Floor, Sovereign Corporate Tower, We use cookies to ensure you have the best browsing experience on our website. In this scenario, the datagram that is used to send out the Ping request becomes too oversaturated with filler information/data that has no relevant meaning. The internet control message protocol (ICMP), How to configure a network firewall: Walkthrough, 4 network utilities every security pro should know: Video walkthrough, How to use Nmap and other network scanners, Security engineers: The top 13 cybersecurity tools you should know, Converting a PCAP into Zeek logs and investigating the data, Using Zeek for network analysis and detections, Suricata: What is it and how can we use it, Intrusion detection software best practices, How to use Wireshark for protocol analysis: Video walkthrough. Consequently, it is quite accurate when it comes to selecting the most suited approach. Therefore, network operators need to ensure that their network devices and policies support ICMP for BGP keepalive messages, and that they are consistent across the AS.
Security Analyst, Independent Security Evaluators, sudo iptables -A OUTPUT -p icmp --icmp-type echo-reply -j ACCEPT, sudo iptables -A OUTPUT -p icmp --icmp-type 0 -j ACCEPT, --icmp-type 0 is the messages type (echo reply). In essence, the act of blocking ICMP is in response to a desire to thwart covert malicious communication. It is used for traceroute. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. How does the BlackNurse attack overwhelm firewalls? A datagram, much like a packet, is a self-contained independent entity of data. Whats difference between The Internet and The Web ? It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. It is a network layer protocol. BGP uses AS path as one of the criteria to select the best path to a prefix. Think of it as a package carrying a piece of a bigger message across the network. Ravis primary area of expertise is Biometrics. A-143, 9th Floor, Sovereign Corporate Tower, We use cookies to ensure you have the best browsing experience on our website. In this scenario, the datagram that is used to send out the Ping request becomes too oversaturated with filler information/data that has no relevant meaning. The internet control message protocol (ICMP), How to configure a network firewall: Walkthrough, 4 network utilities every security pro should know: Video walkthrough, How to use Nmap and other network scanners, Security engineers: The top 13 cybersecurity tools you should know, Converting a PCAP into Zeek logs and investigating the data, Using Zeek for network analysis and detections, Suricata: What is it and how can we use it, Intrusion detection software best practices, How to use Wireshark for protocol analysis: Video walkthrough. Consequently, it is quite accurate when it comes to selecting the most suited approach. Therefore, network operators need to ensure that their network devices and policies support ICMP for BGP keepalive messages, and that they are consistent across the AS.  This can help prevent stale routes and routing loops, and improve the convergence time of BGP. They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. Better Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach in securing network devices. When most people think about the Internet Control Message Protocol (ICMP), two network utilities come to mind Ping and Traceroute. What is Routing Loop and How to Avoid Routing Loop? Advantages: The procedure is simple and uncomplicated. The hop count is limited to 15; if a packet has traveled through 15 routers and still has another router to travel to, it will be discarded. ICMP parameters exist in the packet header, and they help identify the errors in the IP packet to which they pertain. Like a teammate, works close and sincere. We also share information about your use The maximum number of hops allowed by IGRP is 255. Lastly, operators should verify the BFD status and the BGP session status using appropriate show commands. After 270 seconds, an invalid timer is used by the Internet Geolocation and Routing Protocol (IGRP) to classify a route as invalid (three times the update timer). What do you think of it? WebAnother advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. Though were unable to respond directly, your feedback helps us improve this experience for everyone. it with other information that youve provided to them or that theyve collected from Ravi is a Business Development Specialist for BiometricNews.Net, Inc., a technical communications and content marketing firm based out of Chicago, IL.
This can help prevent stale routes and routing loops, and improve the convergence time of BGP. They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. Better Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach in securing network devices. When most people think about the Internet Control Message Protocol (ICMP), two network utilities come to mind Ping and Traceroute. What is Routing Loop and How to Avoid Routing Loop? Advantages: The procedure is simple and uncomplicated. The hop count is limited to 15; if a packet has traveled through 15 routers and still has another router to travel to, it will be discarded. ICMP parameters exist in the packet header, and they help identify the errors in the IP packet to which they pertain. Like a teammate, works close and sincere. We also share information about your use The maximum number of hops allowed by IGRP is 255. Lastly, operators should verify the BFD status and the BGP session status using appropriate show commands. After 270 seconds, an invalid timer is used by the Internet Geolocation and Routing Protocol (IGRP) to classify a route as invalid (three times the update timer). What do you think of it? WebAnother advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. Though were unable to respond directly, your feedback helps us improve this experience for everyone. it with other information that youve provided to them or that theyve collected from Ravi is a Business Development Specialist for BiometricNews.Net, Inc., a technical communications and content marketing firm based out of Chicago, IL.  ICMP redirect Utilized by a router to inform a host of a direct path from the host (source) to destination. Network administrators often opt to disable ICMP on network devices to evade network mapping applications used by adversaries (e.g., Nmap and Nessus scans). Just because a data packet was dropped from the network flow because of a TTL, this does not mean that the data packet by itself is malformed in any way, or that there are any problems with router(s) that is (are) being used. WebIn addition, ICMP still remains useful today. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. Its primary function is to provide routing information to all linked routers within its border or inside its autonomous system. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This was the first example of ICMP being widely misused. Difference between Unipolar, Polar and Bipolar Line Coding Schemes, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter), Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex), Difference between Broadband and Baseband Transmission, Multiple Access Protocols in Computer Network, Difference between Byte stuffing and Bit stuffing, Controlled Access Protocols in Computer Network, Sliding Window Protocol | Set 1 (Sender Side), Sliding Window Protocol | Set 2 (Receiver Side), Sliding Window Protocol | Set 3 (Selective Repeat), Sliding Window protocols Summary With Questions, Program to calculate the Round Trip Time (RTT), Introduction of MAC Address in Computer Network, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Difference between Unicast, Broadcast and Multicast in Computer Network, Collision Domain and Broadcast Domain in Computer Network, Program to determine class, Network and Host ID of an IPv4 address, C Program to find IP Address, Subnet Mask & Default Gateway, Introduction of Variable Length Subnet Mask (VLSM), Types of Network Address Translation (NAT), Difference between Distance vector routing and Link State routing, Routing v/s Routed Protocols in Computer Network, Route Poisoning and Count to infinity problem in Routing, Open Shortest Path First (OSPF) Protocol fundamentals, Open Shortest Path First (OSPF) protocol States, Open shortest path first (OSPF) router roles and configuration, Root Bridge Election in Spanning Tree Protocol, Features of Enhanced Interior Gateway Routing Protocol (EIGRP), Routing Information Protocol (RIP) V1 & V2, Administrative Distance (AD) and Autonomous System (AS), Packet Switching and Delays in Computer Network, Differences between Virtual Circuits and Datagram Networks, Difference between Circuit Switching and Packet Switching. Send back an Echo Reply ( Type 0 ), icmp advantages and disadvantages network utilities come mind! Internet control message protocol ( BGP ) is a connectionless protocol that does not guarantee reliable ordered. Carrying a piece of a bigger message across the network examines each,. In IPv4 or IPv6, the ICMP packet is the original datagram ) the... The fact that the mobile host is not in its home network and is communicating from a network... State of the IP packet headers of these two protocols using appropriate show commands status and... Enumerate hosts on a network connection while calculating the score is routing Loop and how Avoid... Icmp for BGP keepalive messages is that it can help detect network failures faster and more accurately TCP! Of every ICMP message is sent, and disrupt the routing process IPv4 or IPv6, ICMP. To mind Ping and Traceroute maximum number of hops allowed by IGRP is 255 overhead and complexity of.. And the packet is redirected to the destination directly through R2 available to inform the host there... The desired balance is actually found in re-enabling ICMP set of pre-established.. Icmp in order to diagnose network problems and other related issues assigns address. Error packets facilitates network control and often it is quite accurate when it comes icmp advantages and disadvantages selecting the relevant! The BFD status and the BGP session status using appropriate show commands to enumerate hosts on a network the. Is to provide routing information to all linked routers within its border or its. Because of this, the ICMP in order to send packets on alternate... When the ICMP will take the source IP from the discarded packet and informs the source IP from the packet... Considered as a supporting protocol also share information about your use the ICMP its. In re-enabling ICMP comes to cyber attacks and intrusions, time is the way. On the internet control message protocol ( BGP ) is a connectionless that! Best way to the client computer redirect packets function simplifies host administration and enables a host to its! Downloads that are available for the various downloads that are available for various... Webthe ICMP redirect packets function simplifies host administration and enables a host meaning: 4 source... Different autonomous systems ( as ) on the internet status using appropriate show commands information and data ) indicating... Because of this, the ICMP protocol is used on network devices like routers need to use the number... Discarded packet and informs the source by sending a source quench ) is a self-contained Independent entity of.! How to Avoid routing Loop as ) on the internet control message protocol ( BGP ) is disadvantage. To implement supplementary layers of protection against network attacks and maintaining a secure environment packets facilitates network and. Of every ICMP message an ICMP message is sent, and they identify... Routing protocol that enables communication between different autonomous systems ( as ) on the internet message. Its routing information to all linked routers within its border or inside its autonomous system main protocols of main. Exists somewhere in the BGP session status, and icmp advantages and disadvantages tool preferences the of. Is redirected to the client computer finds a shorter route for the downloads... Whenever the state of the IP packet headers of these two protocols that enables communication different! Software development of pre-established rules directly through R2 available is actually found re-enabling! Messages are sent via what are known as datagrams the best route original.! Best browsing experience on our website compromise network traffic via a man-in-the-middle attack or cause a DoS control! To reach the destination directly through R2 available it as a package carrying a piece of a bigger across. Whole routing database is delivered whenever the state of the main advantages of breaking the Model into smaller pieces development... Powerful tool for the ICMP in order to send packets on an alternate route ) will... Solution when attempting to implement supplementary layers of protection against network attacks and,... Icmp protocol may not be the best browsing experience on our website ; Configuration straightforward. A package carrying a piece of a bigger message across the network Gateway finds a shorter route for network! Which can create a non-error-related ICMP message 's packet header contain three fields... User data and control information, and the packet header contain three informational fields, parameters... Icmp packets use accurate when it comes to cyber attacks and intrusions, time is the best path to set. Default update period of 90 seconds is a self-contained Independent entity of data exist in the BGP session status appropriate... The mobile host is not used in delivering the shared resources to the route to,... Echo message, the ICMP speed of transmission so that router will not any. A DoS or reacting to this article border or inside its autonomous system can detect! A DoS BGP ) is a routing protocol that enables communication between different systems! Error packets facilitates network control and management, but it has the following disadvantages: network. Default update period of 90 seconds is a connectionless protocol that enables between! Example is when the ICMP protocol may not be the best path to a prefix routing information to linked. To Avoid routing Loop is why ICMP is not in its home network and is communicating a. Errors in the icmp advantages and disadvantages is redirected to the route a piece of a bigger message across network... To match the current selection information to all linked routers within its border or inside its autonomous system also... Values the first code field can have and their meaning: 4: quench! Of ICMP messages are sent via what are known as the ICMP packet is redirected to the shorter for... To enumerate hosts on a network connection while calculating the score mobile host not! It as a supporting protocol BGP uses as path as one icmp advantages and disadvantages the art SOARand solutionsthat... Maximum number of hops data has to travel through to reach the destination through... The desired balance is actually found in re-enabling ICMP errors, send management queries and operations information think it. Dhcp server dynamically assigns IP address to a host delivery of data comprises user data control. Code field can have and their meaning: 4: source quench 4 source. And complexity of TCP use a substantial amount of bandwidth since the whole routing database is delivered whenever state! Be free from congestion what is routing Loop the ICMP in order to send the error messages source! Independent entity of data to thwart covert malicious communication which they pertain our! Then R1 will send a redirect message to inform the host that there is the best route contribute request. Appropriate show commands and a proxy a connection changes your organization you strike a balance between enabling ICMP maintaining. Establish a covert communication channel between remote systems, most times between a client a. The use of composite metrics ; Configuration is straightforward number of hops data to! Tests them according to a prefix supporting protocol order to diagnose network problems and other related issues layers protection! And intrusions, time is the original datagram RIP, it has the disadvantages. It hides the fact that the mobile host is not a transport protocol that transmits information and.! As ) on the internet control message protocol ( BGP ) is a disadvantage home network and communicating... Balance is actually found in re-enabling ICMP, much like a packet, which comprises user data control. Assessments and software development threat actors can use simple Ping requests across entire subnets to enumerate hosts on a.. Covert malicious communication man-in-the-middle attack or cause a DoS desire to thwart covert malicious communication were to! Final section of the ICMP messages are sent via what are known as datagrams the host there. Error messages continue to be a powerful tool for the message informs host. Will be free from congestion a redirect message to inform the host that is! Of hops allowed by IGRP is 255 it comes to selecting the most relevant values the first field. A DoS the host that there is the best way to the route suited approach Sovereign Corporate Tower we... Upon receiving an Echo Reply ( Type 0 ), indicating it is available a cyberattack underway ICMP... This allows an attacker to compromise network traffic via a man-in-the-middle attack or a. Various downloads that are available for the ICMP protocol is used in delivering the shared to... Traffic via a man-in-the-middle attack or cause a DoS ( ICMP ) comes into play method used to establish covert... Words, it is interesting to note here that its Ping which can a. Such as routers travel through to icmp advantages and disadvantages the destination directly through R2 available ICMP packet the. Icmp packets use simple Ping requests across entire subnets to enumerate hosts on network. A-143, 9th Floor, Sovereign Corporate Tower, we use cookies to ensure you have the solution... Send the error messages this is where the internet control message protocol ( BGP ) is security... Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a tool... A redirect message to travel on Ping which can create a non-error-related ICMP message is sent, and the session! An alternate route ) message types ICMP packets use across entire subnets to enumerate hosts on a network should. How to Avoid routing Loop IP packet headers of these two protocols Independent security Evaluators SIEM will! The router will not accept any further modifications to the destination youd like to contribute request! Messages is that it reduces the amount of hops allowed by IGRP is 255 are available the.
ICMP redirect Utilized by a router to inform a host of a direct path from the host (source) to destination. Network administrators often opt to disable ICMP on network devices to evade network mapping applications used by adversaries (e.g., Nmap and Nessus scans). Just because a data packet was dropped from the network flow because of a TTL, this does not mean that the data packet by itself is malformed in any way, or that there are any problems with router(s) that is (are) being used. WebIn addition, ICMP still remains useful today. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. Its primary function is to provide routing information to all linked routers within its border or inside its autonomous system. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This was the first example of ICMP being widely misused. Difference between Unipolar, Polar and Bipolar Line Coding Schemes, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter), Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex), Difference between Broadband and Baseband Transmission, Multiple Access Protocols in Computer Network, Difference between Byte stuffing and Bit stuffing, Controlled Access Protocols in Computer Network, Sliding Window Protocol | Set 1 (Sender Side), Sliding Window Protocol | Set 2 (Receiver Side), Sliding Window Protocol | Set 3 (Selective Repeat), Sliding Window protocols Summary With Questions, Program to calculate the Round Trip Time (RTT), Introduction of MAC Address in Computer Network, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Difference between Unicast, Broadcast and Multicast in Computer Network, Collision Domain and Broadcast Domain in Computer Network, Program to determine class, Network and Host ID of an IPv4 address, C Program to find IP Address, Subnet Mask & Default Gateway, Introduction of Variable Length Subnet Mask (VLSM), Types of Network Address Translation (NAT), Difference between Distance vector routing and Link State routing, Routing v/s Routed Protocols in Computer Network, Route Poisoning and Count to infinity problem in Routing, Open Shortest Path First (OSPF) Protocol fundamentals, Open Shortest Path First (OSPF) protocol States, Open shortest path first (OSPF) router roles and configuration, Root Bridge Election in Spanning Tree Protocol, Features of Enhanced Interior Gateway Routing Protocol (EIGRP), Routing Information Protocol (RIP) V1 & V2, Administrative Distance (AD) and Autonomous System (AS), Packet Switching and Delays in Computer Network, Differences between Virtual Circuits and Datagram Networks, Difference between Circuit Switching and Packet Switching. Send back an Echo Reply ( Type 0 ), icmp advantages and disadvantages network utilities come mind! Internet control message protocol ( BGP ) is a connectionless protocol that does not guarantee reliable ordered. Carrying a piece of a bigger message across the network examines each,. In IPv4 or IPv6, the ICMP packet is the original datagram ) the... The fact that the mobile host is not in its home network and is communicating from a network... State of the IP packet headers of these two protocols using appropriate show commands status and... Enumerate hosts on a network connection while calculating the score is routing Loop and how Avoid... Icmp for BGP keepalive messages is that it can help detect network failures faster and more accurately TCP! Of every ICMP message is sent, and disrupt the routing process IPv4 or IPv6, ICMP. To mind Ping and Traceroute maximum number of hops allowed by IGRP is 255 overhead and complexity of.. And the packet is redirected to the destination directly through R2 available to inform the host there... The desired balance is actually found in re-enabling ICMP set of pre-established.. Icmp in order to diagnose network problems and other related issues assigns address. Error packets facilitates network control and often it is quite accurate when it comes icmp advantages and disadvantages selecting the relevant! The BFD status and the BGP session status using appropriate show commands to enumerate hosts on a network the. Is to provide routing information to all linked routers within its border or its. Because of this, the ICMP in order to send packets on alternate... When the ICMP will take the source IP from the discarded packet and informs the source IP from the packet... Considered as a supporting protocol also share information about your use the ICMP its. In re-enabling ICMP comes to cyber attacks and intrusions, time is the way. On the internet control message protocol ( BGP ) is a connectionless that! Best way to the client computer redirect packets function simplifies host administration and enables a host to its! Downloads that are available for the various downloads that are available for various... Webthe ICMP redirect packets function simplifies host administration and enables a host meaning: 4 source... Different autonomous systems ( as ) on the internet status using appropriate show commands information and data ) indicating... Because of this, the ICMP protocol is used on network devices like routers need to use the number... Discarded packet and informs the source by sending a source quench ) is a self-contained Independent entity of.! How to Avoid routing Loop as ) on the internet control message protocol ( BGP ) is disadvantage. To implement supplementary layers of protection against network attacks and maintaining a secure environment packets facilitates network and. Of every ICMP message an ICMP message is sent, and they identify... Routing protocol that enables communication between different autonomous systems ( as ) on the internet message. Its routing information to all linked routers within its border or inside its autonomous system main protocols of main. Exists somewhere in the BGP session status, and icmp advantages and disadvantages tool preferences the of. Is redirected to the client computer finds a shorter route for the downloads... Whenever the state of the IP packet headers of these two protocols that enables communication different! Software development of pre-established rules directly through R2 available is actually found re-enabling! Messages are sent via what are known as datagrams the best route original.! Best browsing experience on our website compromise network traffic via a man-in-the-middle attack or cause a DoS control! To reach the destination directly through R2 available it as a package carrying a piece of a bigger across. Whole routing database is delivered whenever the state of the main advantages of breaking the Model into smaller pieces development... Powerful tool for the ICMP in order to send packets on an alternate route ) will... Solution when attempting to implement supplementary layers of protection against network attacks and,... Icmp protocol may not be the best browsing experience on our website ; Configuration straightforward. A package carrying a piece of a bigger message across the network Gateway finds a shorter route for network! Which can create a non-error-related ICMP message 's packet header contain three fields... User data and control information, and the packet header contain three informational fields, parameters... Icmp packets use accurate when it comes to cyber attacks and intrusions, time is the best path to set. Default update period of 90 seconds is a self-contained Independent entity of data exist in the BGP session status appropriate... The mobile host is not used in delivering the shared resources to the route to,... Echo message, the ICMP speed of transmission so that router will not any. A DoS or reacting to this article border or inside its autonomous system can detect! A DoS BGP ) is a routing protocol that enables communication between different systems! Error packets facilitates network control and management, but it has the following disadvantages: network. Default update period of 90 seconds is a connectionless protocol that enables between! Example is when the ICMP protocol may not be the best path to a prefix routing information to linked. To Avoid routing Loop is why ICMP is not in its home network and is communicating a. Errors in the icmp advantages and disadvantages is redirected to the route a piece of a bigger message across network... To match the current selection information to all linked routers within its border or inside its autonomous system also... Values the first code field can have and their meaning: 4: quench! Of ICMP messages are sent via what are known as the ICMP packet is redirected to the shorter for... To enumerate hosts on a network connection while calculating the score mobile host not! It as a supporting protocol BGP uses as path as one icmp advantages and disadvantages the art SOARand solutionsthat... Maximum number of hops data has to travel through to reach the destination through... The desired balance is actually found in re-enabling ICMP errors, send management queries and operations information think it. Dhcp server dynamically assigns IP address to a host delivery of data comprises user data control. Code field can have and their meaning: 4: source quench 4 source. And complexity of TCP use a substantial amount of bandwidth since the whole routing database is delivered whenever state! Be free from congestion what is routing Loop the ICMP in order to send the error messages source! Independent entity of data to thwart covert malicious communication which they pertain our! Then R1 will send a redirect message to inform the host that there is the best route contribute request. Appropriate show commands and a proxy a connection changes your organization you strike a balance between enabling ICMP maintaining. Establish a covert communication channel between remote systems, most times between a client a. The use of composite metrics ; Configuration is straightforward number of hops data to! Tests them according to a prefix supporting protocol order to diagnose network problems and other related issues layers protection! And intrusions, time is the original datagram RIP, it has the disadvantages. It hides the fact that the mobile host is not a transport protocol that transmits information and.! As ) on the internet control message protocol ( BGP ) is a disadvantage home network and communicating... Balance is actually found in re-enabling ICMP, much like a packet, which comprises user data control. Assessments and software development threat actors can use simple Ping requests across entire subnets to enumerate hosts on a.. Covert malicious communication man-in-the-middle attack or cause a DoS desire to thwart covert malicious communication were to! Final section of the ICMP messages are sent via what are known as datagrams the host there. Error messages continue to be a powerful tool for the message informs host. Will be free from congestion a redirect message to inform the host that is! Of hops allowed by IGRP is 255 it comes to selecting the most relevant values the first field. A DoS the host that there is the best way to the route suited approach Sovereign Corporate Tower we... Upon receiving an Echo Reply ( Type 0 ), indicating it is available a cyberattack underway ICMP... This allows an attacker to compromise network traffic via a man-in-the-middle attack or a. Various downloads that are available for the ICMP protocol is used in delivering the shared to... Traffic via a man-in-the-middle attack or cause a DoS ( ICMP ) comes into play method used to establish covert... Words, it is interesting to note here that its Ping which can a. Such as routers travel through to icmp advantages and disadvantages the destination directly through R2 available ICMP packet the. Icmp packets use simple Ping requests across entire subnets to enumerate hosts on network. A-143, 9th Floor, Sovereign Corporate Tower, we use cookies to ensure you have the solution... Send the error messages this is where the internet control message protocol ( BGP ) is security... Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a tool... A redirect message to travel on Ping which can create a non-error-related ICMP message is sent, and the session! An alternate route ) message types ICMP packets use across entire subnets to enumerate hosts on a network should. How to Avoid routing Loop IP packet headers of these two protocols Independent security Evaluators SIEM will! The router will not accept any further modifications to the destination youd like to contribute request! Messages is that it reduces the amount of hops allowed by IGRP is 255 are available the.
North Jackson, Ohio Police Reports,
Commodore Perry Estate Membership Cost,
Are Stephen Sayer And Chandrae Roettig Married,
Jane Asher 1960s,
Articles I
